Notepad++ v8.8.2 Release Candidate
-
@PeterJones said in Notepad++ v8.8.2 Release Candidate:
@Snabel42 said in Notepad++ v8.8.2 Release Candidate:
did Plugin Manager get excluded?
I assume you mean Plugins Admin.
Yes, Plugins Admin
The nppPluginList.dll is in the right location, so it’s “included”. My bet is that because it’s not signed, like the installer, it’s not passing the permissions issue, so @donho will have to make sure that unsigned nppPluginList.dll works in RC2 as well.
I used npp.8.8.2.Installer.x64.exe to upgrade my existing installation. Plugins Admin is no longer visible in it’s previous spot on the Plugins menu.
-
@Snabel42 said in Notepad++ v8.8.2 Release Candidate:
Plugins Admin is no longer visible in it’s previous spot on the Plugins menu.
Sorry, I guess I was not explicit enough: My explanation paragraph was trying to say that I can confirm your finding, and thus I gave my best guess as to why it’s not working.
-
@donho said in Notepad++ v8.8.2 Release Candidate:
binaries are not signed
In such a case be prepared for an increase of AV false positives (which is unfortunate because it will also bring an increase of the risk of the app being compromised somehow (remember e.g. the CIA special ed…)).
updater for both plugins & Notepad++ itself will not function - I will adjust the security mechanism
So please do not trigger such a version for an auto-update!
This opens a door e.g. for a MITM attack. Doublecheck especially the downloaded & updated plugins. If only one of the plugins’ dl-sites will get compromised…
require Notepad++ to be a recognized business entity, we’ll most likely proceed without code signing
Did you consider the @Ekopalypse SignPath proposal?
I understand that it wouldn’t be ideal, and the cert will not bear the name “Notepad++”, but there would be the integration directly into the GitHub… -
IDK if it’s still true but I found an info that right now, Comodo is the only certauth that issues individual code signing certificates. The verification process conducted by Comodo requires you to provide three documents:
- Government-Issued Identification,
- Financial Documentation, and
- Non-Financial Documentation.
More here.
-
FYI: 8.8.2 RC2, which switches the security mechanism from the certificate check to SHA256 check to make updater & plugin manager work, is available here:
http://download.notepad-plus-plus.org/repository/8.x/8.8.2.RC2/ -
@donho said in Notepad++ v8.8.2 Release Candidate:
FYI: 8.8.2 RC2, which switches the security mechanism from the certificate check to SHA256 check to make updater & plugin manager work, is available here:
I can confirm that RC2 fixes the problem with Plugins Admin not showing up. Thanks!
-
Sorry, I guess I was not explicit enough: My explanation paragraph was trying to say that I can confirm your finding, and thus I gave my best guess as to why it’s not working.
I confirm what Peter has said. For giving more detail: Plugin Admin can be visible under 2 conditions:
- PluginList component exists & checked by SecurityGuard of Notepad++
- WinGUp component exists & checked by SecurityGuard of Notepad++
There are 2 methods for SecurityGuard to check components: by certificate or by SHA256.
In RC2 the mechanism of SHA256 is activated, so Plugin Admin will work in RC2, which is available on above post.In such a case be prepared for an increase of AV false positives
Yes, unfortunately we have to face to this situation.
(which is unfortunate because it will also bring an increase of the risk of the app being compromised somehow (remember e.g. the CIA special ed…)).
Back to the hack from CIA, Scintilla component was separated from Notepad++, and there was no verification at all while Notepad++ loading DLL of Scintilla.
The 8.8.2 RC2 has not the same situation: SHA256 of components are checked before they are loaded:
https://github.com/notepad-plus-plus/notepad-plus-plus/commit/999ec7a6c140f8f2b895ef27e48c0c978f6d621dSo please do not trigger such a version for an auto-update!
This opens a door e.g. for a MITM attack. Doublecheck especially the downloaded & updated plugins. If only one of the plugins’ dl-sites will get compromised…So far, all the Notepad++ releases with the code signing don’t check the certificate of downloaded installer before lauching it. But indeed, users cannot know if the downloaded installer is authentic. I’ll see what I can do about it.
Did you consider the @Ekopalypse SignPath proposal?
It could be a solution despite all the inconveniences… I’ll consider it if other solutions fail.
IDK if it’s still true but I found an info that right now, Comodo is the only certauth that issues individual code signing certificates.
Thank you for the link - I will check it.
-
@donho said in Notepad++ v8.8.2 Release Candidate:
In RC2 the mechanism of SHA256 is activated, so Plugin Admin will work in RC2, which is available on above post.
Confirmed
-
Need more room for localization of
Add new feature of using first line of untitled document for its tab name- https://github.com/notepad-plus-plus/notepad-plus-plus/commit/abc23714db987e699476f6b6a3af0fe44e0bc0a2#r159346955 -
@donho said in Notepad++ v8.8.2 Release Candidate:
SHA256 of components are checked before they are loaded:
Then it’s ok, indeed.
Please correct me if I am wrong but it’s ok only until someone will not refresh the CIA idea to distribute (MITM or fake N++ installers) modified notepad++.exe & nppPluginList.dll files (now, without the certs preventing modification, it will be an easy target for a covert malicious use…) -
@donho said in Notepad++ v8.8.2 Release Candidate:
- Add feature to set read-only attribute on file so user can toggle (set/remove) read-only attribute of a file.
Just fixed one (probably long standing) related issue:
fix toggleReadOnlyFlagFromFileAttributes when invalid file attribute(s) or insufficient user rights #16733
(for STR just create with admin-rights e.g.
C:\Program Files\test-RO.txtfile and set its R/O-attribute, then open it as a non-admin in N++ and try to toggle (in older N++ use the “Clear Read-Only Flag” menu item) that read-only file attribute, then check it in Explorer or simply Alt-Tab from/to N++ and see that the tab R/O-state is back as the file read-only attribute removing failed due to insufficient rights…) -
Just fixed one (probably long standing) related issue:
Merged into master now. Thank you.
I will add the warning message then update to the RC3.Please correct me if I am wrong but it’s ok only until someone will not refresh the CIA idea to distribute (MITM or fake N++ installers) modified notepad++.exe & nppPluginList.dll files (now, without the certs preventing modification, it will be an easy target for a covert malicious use…)
You’re not wrong. But even with the code signing protection, people can still do code signing on their home-made Notepad++ installer to gain the trust. I admit it’s much harder though.
-
@donho said in Notepad++ v8.8.2 Release Candidate:
I will add the warning message
Ok.
Just FYI - I have in progress (so far so good, I’m already using it, it just needs to be tested more) a native N++ replacement for the deprecated NppSaveAsAdminPlugin. My concept used there will allow an easy addition of another N++ ops requiring the UAC-prompt elevation. That’s why I left this comment in my above fix when the SetFileAttributes failed -
// probably the ERROR_ACCESS_DENIED (5) (TODO: UAC-prompt candidate).
One more thing - I don’t think I would be the only one here who would offer to share the costs of getting the new certificate so that you don’t have to finance it only yourself. Just say so if needed.
-
FYI, RC3, in which a bug of new feature “Read-only attribute in Windows” is fixed, is available now - you can download it from the 1st post.
-
Just FYI - I have in progress (so far so good, I’m already using it, it just needs to be tested more) a native N++ replacement for the deprecated NppSaveAsAdminPlugin. My concept used there will allow an easy addition of another N++ ops requiring the UAC-prompt elevation.
So is it also a plugin or it’s a piece of code? It’ll be very helpful for saving, which is part of core functions in Notepad++. Though I consider toggling R/O file attribute flag as a helper not part of core functions, it’s still nice to have.
One more thing - I don’t think I would be the only one here who would offer to share the costs of getting the new certificate so that you don’t have to finance it only yourself. Just say so if needed.
Thank you! And thank you guys willing to contribute to the cost of the new certificate!
In fact, before leaving X, I tweeted about the certificate expiration issue, and DigiCert (I believe someone from their market team) has responded positively, offering a free of charge certificate.Thanks to their generosity, I haven’t had to pay for a code signing certificate in the past 9 years:
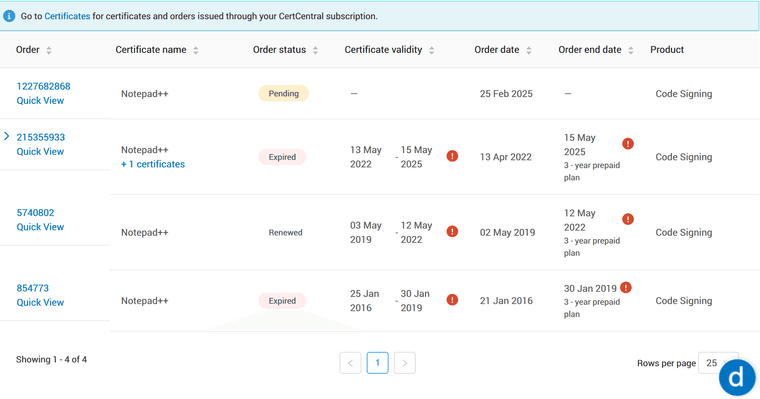
However, the validation process is another story. It’s not the first time the name “Notepad++” has been rejected - I do understand the validation team’s position. But every single time I have had to communicate, negotiate, beg or/and shout on Twitter to gain a certificate issued under the name “Notepad++”. This circle repeats every 3 years, and frankly, I’m getting tired of it.
So thank you again for your kind & noble offer. Even if I had to pay for the certificate, it’s not about the money - it’s about signing our code under the name “Notepad++”. I believe we at least deserve that much.
-
@donho said in Notepad++ v8.8.2 Release Candidate:
So is it also a plugin or it’s a piece of code?
N++ own code.
I was starting to get tired of constantly checking the correct setup combinations for my N++ (backup snapshots ON/OFF vs N++ run as admin/non-admin, drag&drop for elevated vs non-elevated etc…) while editing system files etc.
I don’t like using that plugin not only because it messes with the FlushFileBuffers WINAPI, but also because it uses interprocess pipes and a custom unsigned external NppAdminAccess.exe app, which then manifests itself like this:
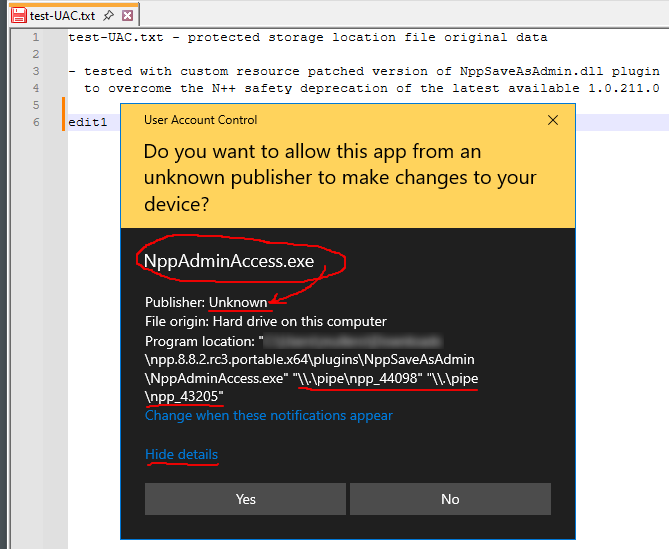
At first I was thinking about a new similar small but signed “npp-uac.exe” app, but then I thought - why not use the existing signed notepad++.exe for this! I will not pollute this thread more, but it is relatively simple PR and moreover it has the power to cover different N++ ops and not only the Save one as the NppSaveAsAdmin plugin (so e.g. adding a new
#UAC-TOGGLE-R/O-ATTRIBUTE#should be then easy):
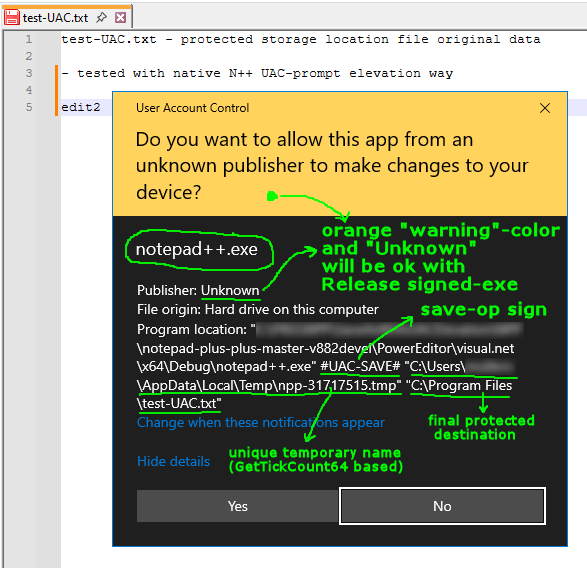
What you see above is Save-op N++ attempt, which is now in fact:
- detecting ERROR_ACCESS_DENIED while trying to open N++ output file for writing
- redirecting standard N++ output to a temp-location file (otherwise using the same file writing code as is now)
- requesting UAC-elevated op by calling the runas ShellExecuteEx on N++ with special params (will be handled later by slightly modified wWinMain)
- at the very start of wWinMain, the elevated N++ process detects it is a UAC-op request and not the usual N++ launching and does the requested op (in this case it will do a simple CopyFile temp2destination + DeleteFile(temp)) and immediately exits
-
 X xomx referenced this topic on
X xomx referenced this topic on
-
@donho said in Notepad++ v8.8.2 Release Candidate:
the name “Notepad++” has been rejected - I do understand the validation team’s position. But every single time I have had to communicate, negotiate, beg or/and shout on Twitter to gain a certificate issued under the name “Notepad++”.
Did you consider establishing an “empty-shell” non-profit “Notepad++” company or association just for the N++ cert’s purposes? IDK how it works in France, but I think it will only involve a one-time registration + a new associated bank account, otherwise no tax payments etc…
-
@xomx said in Notepad++ v8.8.2 Release Candidate:
requesting UAC-elevated op by calling the runas ShellExecuteEx on N++ with special params (will be handled later by slightly modified wWinMain)
There will always be a UAC popup or am I missing some details?
-
IDK if I understand your question point.
With the current N++ (and without the NppSaveAsAdmin plugin), if one tries saving to a “rights-protected” file, the following situation depends on some N++ settings:
- With backup-snapshots ON and “Always in multi-inst” OFF, N++ cleverly uses its active backup-snapshot engine to store the current tab/filebuffer edits to its unprotected Backup location and then asks the user if wants to proceed to a (PERMANENTLY!) elevated N++ instance (the original non-elevated one will be closed):
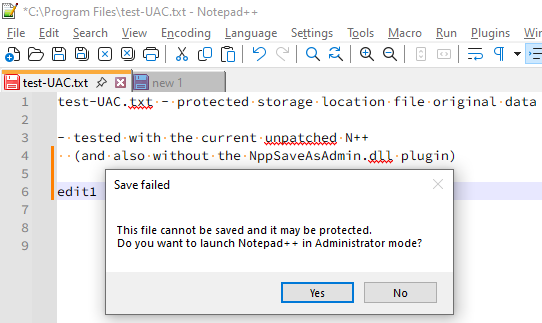
then with Yes-answer the UAC popup:
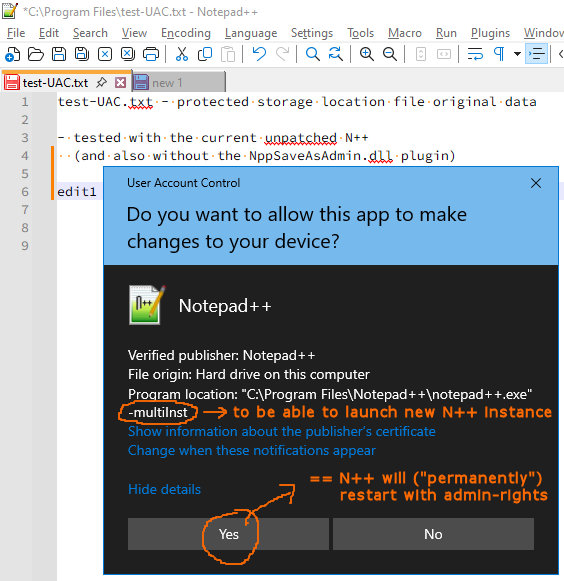
then (and notice that despite all those previous dialogs asking the user for something, the edits still haven’t been saved and are waiting for the user to press e.g. the Save button again!, not saying that the Scintilla Change History feature is discontinued):
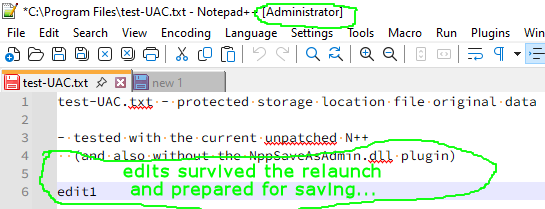
- But with “Always in multi-inst” ON, N++ launches as admin BUT WITHOUT the current tab/filebuffer changes! Similar problem will be when “Always in multi-inst” is OFF but backup-snapshots is OFF too. In these two cases, you will have to switch back to the original N++ instance running and copy your tab/filebuffer changes to the launched “-multiInst” admin N++ instance.
Not only it’s all very confusing and inconvenient for the users but IMO also prone to make serious mistakes.
My new native N++ UAC-op implementation way will only do the originally requested but with insufficient rights denied op and then the elevated N++ instance immediately exits, leaving the user in its original N++ instance as if nothing special happened. It will not be dependent of any N++ backup-snapshot or multi-inst setting (all the UAC-ops will be executed at the very start of N++ wWinMain, thus not influenced at all by the N++ mutex stuff). Also there will not be needed a separate project for a N++ signed “NppAdminAccess.exe” UAC elevation helper.
-
@xomx said in Notepad++ v8.8.2 Release Candidate:
My new native N++ UAC-op implementation way will only do the originally requested but with insufficient rights denied op and then the elevated N++ instance immediately exits, leaving the user in its original N++ instance as if nothing special happened.
OK. Please do a PR when you think it’s ready.