Notepad++ v8.8.3 Release Candidate
-
There were - and still are - many false positives reported in the v8.8.2 binaries by the antivirus software. To prevent this issue from recurring in future releases, this version is signed with a certificate issued by a self-signed Certificate Authority (CA). The root certificate (i.e., the CA in question) will be published on the Notepad++ website & GitHub repository, allowing antivirus vendors and users to verify the authencity of each release.
There should be no regressions in this release. It will be published as soon as I finish writting the release notes, explaining the new self-signed certificate and creating a guide on installation the Notepad++ root certificate. The process may take arround 2 days.
For those who want to install Notepad++ root certificate in his PC, here is the certificate:
http://download.notepad-plus-plus.org/repository/MISC/xca/Notepad_plus_plus_Root_Certificat.crt
It will be great If you can also provide the guide ;)Notepad++ 8.8.3 RC is available here:
http://download.notepad-plus-plus.org/repository/8.x/8.8.3.RC/
http://download.notepad-plus-plus.org/repository/8.x/8.8.3.RC2/
http://download.notepad-plus-plus.org/repository/8.x/8.8.3.RC3/
http://download.notepad-plus-plus.org/repository/8.x/8.8.3.RC4/
http://download.notepad-plus-plus.org/repository/8.x/8.8.3.RC5/Notepad++ v8.8.3 security-fixes & new enhancement:
- Use self-signed certificate to sign new release binaries. (Implement commit)
- Fix uninstaller security issue (CVE-2025-49144). (Fix #16787)
- Enhance security for DLL loading. (Fix #13964)
Notepad++ v8.8.2 regression-fixes, bug-fixes & new features:
- Fix regression of folding state not being remembered through sessions. (Fix #16597, #16670)
- Fix “Go To Settings” links in Style Configurator regression (from v8.8). (Fix #16592)
- Fix small regression of tab background (hovered) highlighting issue after drag&drop. (Fix #16559)
- Fix an unresponsive (hang) issue due to hide lines. (Fix #16316)
- Fix installer security issue by using the absolute path instead of an unspecified path (CVE-2025-49144). (commit, fix report on GitHub, fix #16744)
- Installer component “WinGUp”: update cURL to 8.13.0 for fixing cURL’s security issue CVE-2025-0167. (Fix #16531, #16515)
- Update to scintilla 5.5.7 & Lexilla 5.4.5. (Implement #16649)
- Add feature to update Notepad++ on exit. (Fix #16601, #13749, #10317, #8495, #8457, #3755)
- Add “/relaunchNppAfterSilentInstall” command argument for installer. (Fix #issue)
- Add feature to set read-only attribute on file so user can toggle (set/remove) read-only attribute of a file. (Fix #326, #4594, #6216, #7841, #12520, #15571, #16603)
- Add new plugin API: NPPM_GETTOOLBARICONSETMODE & NPPN_TOOLBARICONSETCHANGED to get toolbar icon set choice. (Fix #16547, #16646)
- Deprecate 3 APIs: Deprecate NPPM_GETOPENFILENAMES, NPPM_GETOPENFILENAMESPRIMARY & NPPM_GETOPENFILENAMESSECOND. (Fix #15997)
- Add new feature of using first line of untitled document for its tab name. (Fix #3994, #16584)
- Enhance NPPM_DARKMODESUBCLASSANDTHEME: Enable darkmode progress bar for plugins. (Fix #16675)
- Various dark mode enhancements. (Fix #16668, #16674, #16560, #16537, #issue)
- Fix right click on caption bar unhidding main menu. (Fix #16652)
- Fix rename tab error message when tab name is unchanged. (Fix #16661)
- Fix Python FunctionList absorbing next function issue if space after colon. (Fix #16636)
- Remove .log from errorlist lexer’s default extensions. (Fix #16627)
- Make raw string syntax highlighting work for Golang. (Fix #16609)
- Fix Notepad++ tray icon lost after Windows Taskbar crashing & being relaunched. (Fix #16588)
- Fix changing toolbar icon set not updating to matching panel icon set. (Fix #16595)
- Fix Windows dialog file list not react with keystroke (character match). (Fix #2239)
- Add “*” mark on modified file entries in “Windows” dropdown menu. (Fix #16542)
-
@donho said in Notepad++ v8.8.3 Release Candidate:
this version is signed with a certificate issued by a self-signed Certificate Authority (CA).
Hmm… I am not seeing the installer or executable be signed.
- I downloaded the http://download.notepad-plus-plus.org/repository/8.x/8.8.3.RC/npp.8.8.3.Installer.x64.exe
- right click, Properties, Digital Signatures, and it’s showing none. (Whereas when I look at the npp.8.8.1.Installer.x64.exe, I see the digital signature on that one)
- try running the installer, and Windows complains about unknown publisher (just like it did for the npp.8.8.2.Installer.x64.exe, which was unsigned)
- I downloaded the portable http://download.notepad-plus-plus.org/repository/8.x/8.8.3.RC/npp.8.8.3.portable.x64.zip
- unzip the notepad++.exe from there
- right click, Properties, Digital Signatures, and it’s showing no signatures as well.
I thought maybe it was because I didn’t have your CA certificate yet, so I installed that, then tried the above again: both of those still show as unsigned.
So I don’t know if I’ve done something wrong, or if you accidentally uploaded the unsigned copies…
here is the certificate: http://download.notepad-plus-plus.org …
Word of warning: that’s a non-HTTPS URL. It would really behoove you to publish the certificate on a site where HTTPS is available – maybe on your main https://notepad-plus-plus.org site instead. Without that, there can be no confidence that there isn’t a man-in-the-middle attack, injecting a false certificate; without an https URL, it is doubtful whether antivirus vendors would ever trust your CA certificate, or any signing-certificate generated from that CA.
It will be great If you can also provide the guide ;)
This much, I got working:
Caveat emptor: Only follow these instructions if you trust the download path between the server and your computer, and if you trust software or certificates that @donho has signed
- Download the .crt file
- If I click on the link, it just opens the
about:blanktab – I think my browser might be trying to protect me from unexpected certificates - Instead, right click on the link and Save As. Your browser may protect you: if it pops up something saying it’s unsafe, you can click Keep (that’s what Chrome says, anyway; use whatever your browser’s nomenclature is). (I think that an
https://URL might have avoided that extra rigmarole)
- If I click on the link, it just opens the
- Open the certificate: double-click, or right-click > Open
- if Windows is confused on your machine, you might have to Open With and choose “Crypto Shell Extensions”
- Once it’s open
- The Certification Path tab will say it’s untrusted at this point
- On the main General tab, click Install Certificate
- ick “Current User”, NEXT
- don’t pick “Automatically select…” because it will default to “Intermediate Certification Authorities”, which isn’t sufficient for a self-signed
- pick “Place all certificates in the following store”, and Browse to
Trusted Root Certification Authorities, NEXT - FINISH
- There will be a warning, because you are putting it in Trusted Root CA. Make sure you understand the implications of moving forward with YES.
- “The import was successful”: OK
- If you close the Certificate, then open it again, the General tab shows the certificate’s purpose, and the Certification Path will show it’s trusted.
- If you ever want to remove that Trusted Root CA certificate (for example, if you stop trusting Don’s signature, or he is able to get a public CA to behave reasonably toward open source developers)
Win+Rto bring up Run dialog, and runcertmgr.msc- Navigate to
Trusted Root Certification Authorities>Certificates - Scroll down until you find “Notepad++ Root Certificate”, and right click on it, then Delete and Yes
- I downloaded the http://download.notepad-plus-plus.org/repository/8.x/8.8.3.RC/npp.8.8.3.Installer.x64.exe
-
@PeterJones said in Notepad++ v8.8.3 Release Candidate:
Hmm… I am not seeing the installer or executable be signed.
Sorry about that - I have disabled code signing for the build package while testing PR #16787 and verify the functionality of the unstaller. I forgot to re-enabke signing after merging PR #16787.
After building RC1, instead of checking for the certificate in the binaries (which I have already done several times), I focused only 2 commands: “Update Notepad++” & “Plugins Admin…” - since without signature on gup.exe & nppPluginList.dll, these command don’t work. However, both of these files were signed before the latest RC1 build.
Not trying to make excuses, just clarify the context.RC2 is available here: http://download.notepad-plus-plus.org/repository/8.x/8.8.3.RC2/
Word of warning: that’s a non-HTTPS URL. It would really behoove you to publish the certificate on a site where HTTPS is available – maybe on your main https://notepad-plus-plus.org site instead. Without that, there can be no confidence that there isn’t a man-in-the-middle attack, injecting a false certificate; without an https URL, it is doubtful whether antivirus vendors would ever trust your CA certificate, or any signing-certificate generated from that CA.
X509 Notepad++ Root Certificate will be published here:
https://notepad-plus-plus.org/notepadroot.crtBTW, I should make https work, I know - it’s on my TODO list.
This much, I got working:
Thank you! It deserves also in npp-user-manual.org - what do you think?
-
BTW, I should make https work, I know - it’s on my TODO list.
Good idea. :-)
Thank you! It deserves also in npp-user-manual.org - what do you think?
Yes, makes sense. I am adding those instructions (cleaned up) to the Getting Started page.
X509 Notepad++ Root Certificate will be published here:
https://notepad-plus-plus.org/notepadroot.crtLet me know once it’s available at that URL, and I’ll push the new instructions to the Manual website.
-
@PeterJones and others - Is the self-signed root cert going to be the permanent fix? It seems a lot of work being put into this by you and others.
I have hoped that Notepad++ will soon get signed again via a normal CA.
Related to that is will the https certificate for https://download.notepad-plus-plus.org/ will get renewed? It expired five years ago on Sat, 22 Feb 2020 19:46:00 GMT.
-
Related to that is will the https certificate for https://download.notepad-plus-plus.org/ will get renewed? It expired five years ago on Sat, 22 Feb 2020 19:46:00 GMT.
Considering @donho said above, “BTW, I should make https work, I know - it’s on my TODO list.”, I can confidentally conclude that the goal is to get it renewed. ;-)
Is the self-signed root cert going to be the permanent fix?
My guess is that’s currently unknowable. It presumably depends on how long beaurocracy fights Don vs how much effort he is willing to expend.
Given the number of complaints since v8.8.2, I think it’s worth the effort (at least, my tiny side of the effort) until such time as a different CA can be used: even if it’s only 1 version down the road (so a month later), saving that month of signed-installer posts will be worth it to me. :-)
-
@mkupper said in Notepad++ v8.8.3 Release Candidate:
Is the self-signed root cert going to be the permanent fix?
I hope not. In the long term, a public trusted CA cert is needed, such as the previously used DigiCert one.
But using a self-signed certificate is much much better from the BFU’s (or the Don’s grand-mom ;-) ) POV.
No one can expect that BFU will install Kleopatra (and create the needed OpenPGP key pair etc etc…!) to verify the N++ distributed sigs. But using the standard Windows Explorer and Certificate interface for checking of the N++ executable digital signature == ok, even if “unverifiable” for now:
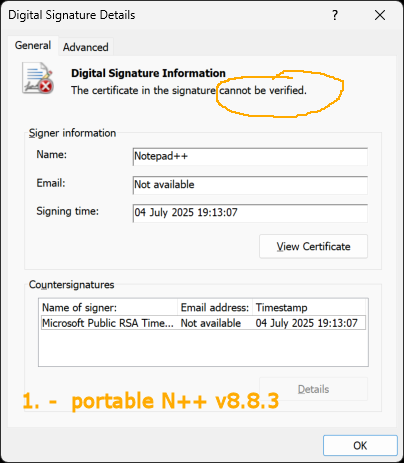
it’s a halfway where to go (BTW I saw somewhere that some corporate takes an unsigned 3rd party app and signed it with their own MS Azure self-signed cert just for an internal re-distribution).
IMO - even if the above (very good!) description, for adding the N++ own cert to the trusted root ones, is not for every BFU in general, it’s still much better than want from them to learn how the OpenPGP (and public/private key stuff) works.
After N++ is in Trusted Root CA: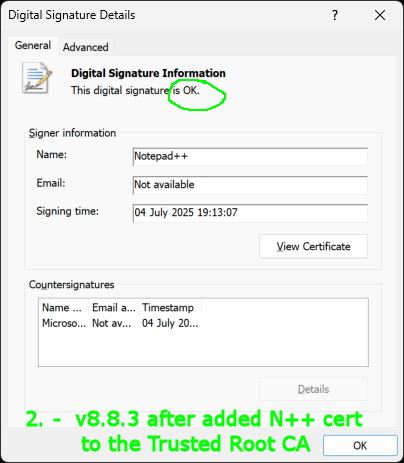
Now the N++ executables:
- can be trusted (verified the origin, with some acceptable effort)
- prevents unnoticed modifications (common disk storage corruptions but also malicious modifs):
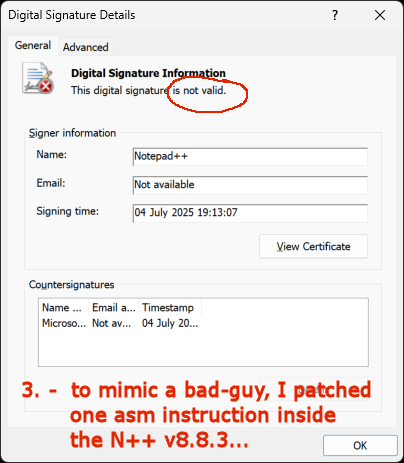
(Sidenote: I’d not overestimate the executables digital sign in the malware fighting - nowadays many sophisticated attacks use patching already loaded process in memory and so they do not touch the executable files on disk at all…)
-
FYI, an error has been found in the certificates, so the root certificate and code signing certificate have been regenerated, and v8.8.3 RC binaries are signed again:
http://download.notepad-plus-plus.org/repository/8.x/8.8.3.RC3/You can download both Notepad++ Root Certificate & Notepad++ Revocation list from the root of https://notepad-plus-plus.org.
-
@donho How does one remove the previous one? I can’t find the previous (bad) certificate in the certification manager. Oh, and the revocation link doesn’t work: no file.
-
@Graham-Norris said in Notepad++ v8.8.3 Release Candidate:
Oh, and the revocation link doesn’t work: no file.
Fixed now.
-
@Graham-Norris said in Notepad++ v8.8.3 Release Candidate:
I can’t find the previous (bad) certificate in the certification manager.
Maybe you used for the N++ cert “Store location”
Local Machineinstead of theCurrent User?If so, try to launch “certlm.msc” MMC snap-in instead of the above mentioned “certmgr.msc”.
-
The latest, and I believe the last update:
http://download.notepad-plus-plus.org/repository/8.x/8.8.3.RC4/Very sorry about that. Some errors have been found in the certificate and I have had to regenerate the ROOT CA & the signing certificate.
Anyway, it seems all OK now, so I can promise you it’s the last one. -
@xomx Thank you. When I downloaded and installed the certificate from https://notepad-plus-plus.org/nppRoot.crt that the installer process popped up:
--------------------------- Security Warning --------------------------- You are about to install a certificate from a certification authority (CA) claiming to represent: Notepad++ Windows cannot validate that the certificate is actually from "Notepad++". You should confirm its origin by contacting "Notepad++". The following number will assist you in this process: Thumbprint (sha1): C4E7785B 6DD1DAF2 AEDE5C99 4BB3D495 AF7B45AB Warning: If you install this root certificate, Windows will automatically trust any certificate issued by this CA. Installing a certificate with an unconfirmed thumbprint is a security risk. If you click "Yes" you acknowledge this risk. Do you want to install this certificate? --------------------------- Yes No ---------------------------The thumbprint
C4E7785B 6DD1DAF2 AEDE5C99 4BB3D495 AF7B45ABis not mentioned in the user manual. I tried Google for “C4E7785B 6DD1DAF2 AEDE5C99 4BB3D495 AF7B45AB” and then “C4E7785B6DD1DAF2AEDE5C994BB3D495AF7B45AB” but it was not found. -
I have no issue with v8.8.2
But with v8.8.3 (all RC), installed the cert. (checked in Local Machine & Current User), i have the issue (newly program detected) by Trend Apex One (my company).
Thanks for your support, Notepad++ is my favorite editor. I’m currenty using portable edition.
-
@mkupper said in Notepad++ v8.8.3 Release Candidate:
The thumbprint C4E7785B 6DD1DAF2 AEDE5C99 4BB3D495 AF7B45AB is not mentioned
@donho , did you want to add the links to the Root CA and CRL files on https://notepad-plus-plus.org/resources/ , along with the thumbprints for the Root CA and the current signing certificate you are using?
Since you have the GPG there, it makes sense to also share the details of the new CA and signing certs there as well.
I could then have the Manual link to that page for people to confirm the thumbprints for the certs.
-
@PeterJones said in Notepad++ v8.8.3 Release Candidate:
@donho , did you want to add the links to the Root CA and CRL files on https://notepad-plus-plus.org/resources/ , along with the thumbprints for the Root CA and the current signing certificate you are using?
The paths of revocation list (crl) and root certificate are indicated in the Notepad++ code signing certificate (you can find them in the section “Details”):
CRL Distribution Point:
[1]CRL Distribution Point Distribution Point Name: Full Name: URL=http://notepad-plus-plus.org/nppRevoke.crlAuthority Information Access:
[1]Authority Info Access Access Method=Certification Authority Issuer (1.3.6.1.5.5.7.48.2) Alternative Name: URL=http://notepad-plus-plus.org/nppRoot.crtSo, firstly if we want to move these 2 files to resources directory, this code signing certificate should be revoked, then a new certificate can be regenerated with 2 modified paths. the RC should be signed again and RC5 should be checked again by the community…
Secondly, since such information is imposed by the certificate, for me
URL=http://notepad-plus-plus.org/nppRoot.crt
looks more serious then
URL=http://notepad-plus-plus.org/resources/nppRoot.crt,
and they are more accessible for the antivirus vendors, IT ppl & users (just under the root - shorter and simpler).For the above reasons, let’s keep it as it is. If it’s really bothering, we can always change in 3 years.
-
@donho ,
Sorry, I think I didn’t communicate clearly enough. I meant add a paragraph/section to the page at https://notepad-plus-plus.org/resources/ , which will link to the files which can stay at
https://notepad-plus-plus.org/nppRoot.crtandhttps://notepad-plus-plus.org/resources/nppRoot.crt, and give details about those files, just like you do for the “Release Key”. Something like: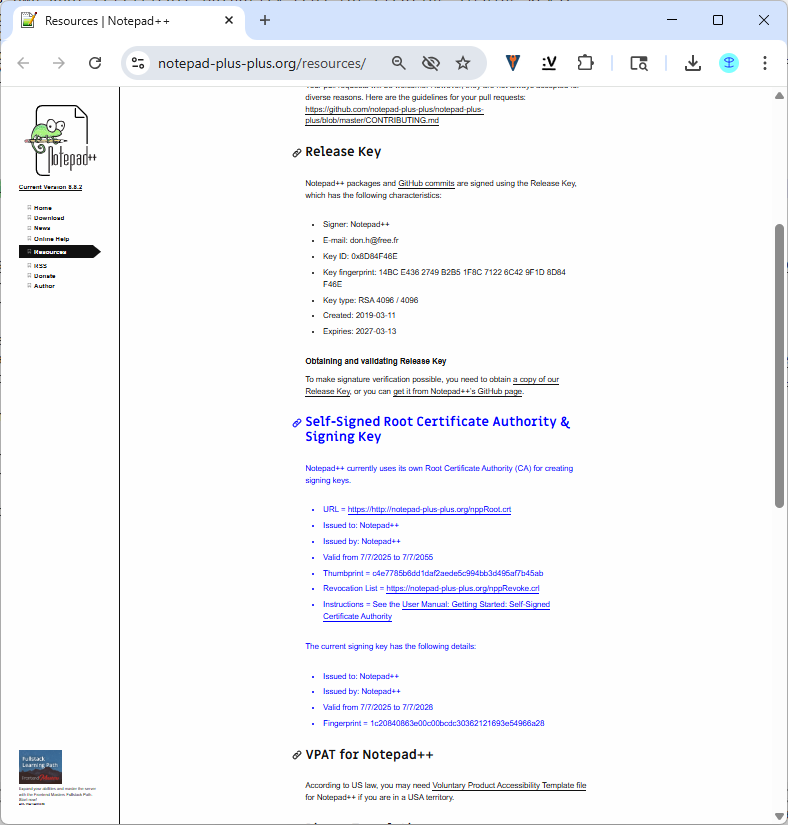
You don’t have to use exactly that phrasing – I just mocked it up similar to what you had in the earlier section on that page.
<h2>Self-Signed Root Certificate Authority & Signing Key</h2> <p>Notepad++ currently uses its own Root Certificate Authority (CA) for creating signing keys. </p> <ul> <li>URL = <a href="https://http://notepad-plus-plus.org/nppRoot.crt">https://http://notepad-plus-plus.org/nppRoot.crt</a></li> <li>Issued to: Notepad++</li> <li>Issued by: Notepad++</li> <li>Valid from 7/7/2025 to 7/7/2055</li> <li>Thumbprint = <tt>c4e7785b6dd1daf2aede5c994bb3d495af7b45ab</tt></li> <li>Revocation List = <a href="https://notepad-plus-plus.org/nppRevoke.crl">https://notepad-plus-plus.org/nppRevoke.crl</a></li> <li>Instructions = See the <a href="https://npp-user-manual.org/docs/getting-started/#notepad-self-signed-certificate-authority-for-binaries">User Manual: Getting Started: Self-Signed Certificate Authority</a></li> </ul> <p>The current signing certificate has the following details:</p> <ul> <li>Issued to: Notepad++</li> <li>Issued by: Notepad++</li> <li>Valid from 7/7/2025 to 7/7/2028</li> <li>Thumbprint = <tt>1c20840863e00c00bcdc30362121693e54966a28</tt></li> </ul>This information will allow people to verify that they have correctly downloaded the right Root Certificate Authority, similar to the way you let them verify the GPG signature.
To sum up: I wasn’t asking you to change the URL of the certs or to re-issue them. I was asking you to publish the data about them on the main website, similar to the way you publish the data about the GPG signature on the main website.
-
@PeterJones said in Notepad++ v8.8.3 Release Candidate:
You don’t have to use exactly that phrasing – I just mocked it up similar to what you had in the earlier section on that page.
Yes, you’re right - I forgot the part of resources!
I will add the information into this page, so it will be available during the release process.
Thank you for the reminding! -
@donho said in Notepad++ v8.8.3 Release Candidate:
URL=http://notepad-plus-plus.org/nppRevoke.crl
URL=http://notepad-plus-plus.org/nppRoot.crt
Maybe I’m a little bit lost in all that RC versions, but now I dl again the RC4 ones x64 installer and it’s signed like the above statements, which is just wrong, isn’t it? (should be with
httpsinstead):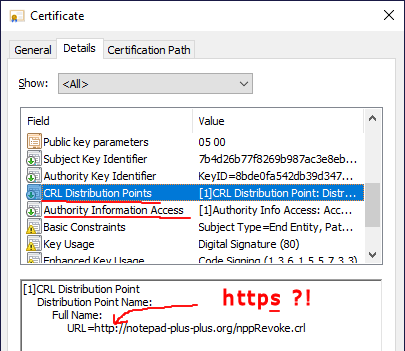
Edit: Seems like MS own signed executables have the same http-only.
-
@xomx said in Notepad++ v8.8.3 Release Candidate:
Maybe I’m a little bit lost in all that RC versions, but now I dl again the RC4 ones x64 installer and it’s signed like the above statements, which is just wrong, isn’t it? (should be with https instead):
The use of “http” instead of “https” wasn’t a mistake - that’s simply how it was done. You can check other digitally signed programs to confirm this.
In RC5280 “Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile”, Security Considerations section:
CAs SHOULD NOT include URIs that specify https, ldaps, or similar schemes in extensions. CAs that include an https URI in one of these extensions MUST ensure that the server's certificate can be validated without using the information that is pointed to by the URI. Relying parties that choose to validate the server's certificate when obtaining information pointed to by an https URI in the cRLDistributionPoints, authorityInfoAccess, or subjectInfoAccess extensions MUST be prepared for the possibility that this will result in unbounded recursion.