VirusTotal.Com Analysis of npp.8.1.9.2.Installer.x64.exe Reports "Detects executables signed with stolen, revoked or invalid certificates"
-
Hello,
After I download npp.8.1.9.2.Installer.x64.exe, I uploaded it to TotalVirus.com for analysis, and the site reported
-
Matches rule INDICATOR_KB_CERT_01342592a0010cb1109c11c0519cfd24 by ditekSHen from ruleset indicator_knownbad_certs at https://github.com/ditekshen/detection
Detects executables signed with stolen, revoked or invalid certificates -
Matches rule INDICATOR_KB_CERT_01342592a0010cb1109c11c0519cfd24 by ditekSHen from ruleset indicator_knownbad_certs at https://github.com/ditekshen/detection
Detects executables signed with stolen, revoked or invalid certificates -
Matches rule AutoIT_Script by @bartblaze from ruleset AutoIT at https://github.com/bartblaze/Yara-rules
Identifies AutoIT script.
Could I get some feedback?
Details:
- I downloaded the file from: https://github.com/notepad-plus-plus/notepad-plus-plus/releases/download/v8.1.9.2/npp.8.1.9.2.Installer.x64.exe
- You can view the VirusTotal report @ https://www.virustotal.com/gui/file/2bb2c7bca2b2ad54701c15cabcbc336643f3829d33d3411c0fb8f75ab1bfa1a0/detection
- The SHA256 of this file, matches the one published @ https://github.com/notepad-plus-plus/notepad-plus-plus/releases/tag/v8.1.9.2
** IN OTHER WORDS, the SHA256 of the file is 2bb2c7bca2b2ad54701c15cabcbc336643f3829d33d3411c0fb8f75ab1bfa1a0
-
-
Could I get some feedback?
Sorry, when I look at the https://www.virustotal.com/gui/file/2bb2c7bca2b2ad54701c15cabcbc336643f3829d33d3411c0fb8f75ab1bfa1a0/detection link that you provided, I don’t see any of the warnings that you saw. Where exactly are those warnings/errors/rule-lists?
The detection page has nothing but green checkmarks.
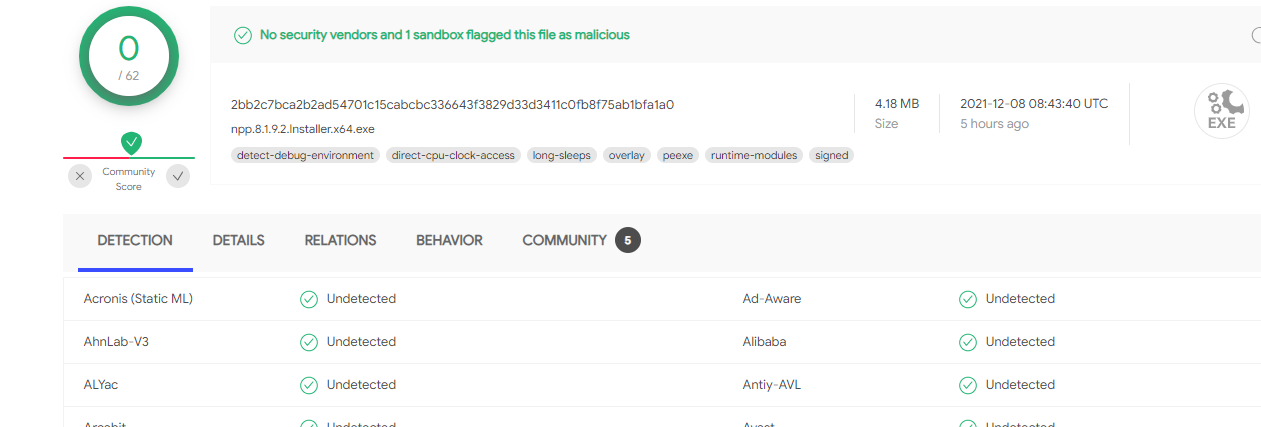
The details page says the signature is good.
I don’t see “ditekshen” anywhere on the page, nor “indicator_knownbad_certs” nor any of the INDICATOR_KB_CERT_### that you show (or any others), nor “AutoIT_Script” nor “@bartblaze”.
As far as I can tell from that report, VirusTotal doesn’t think anything is wrong with the Notepad++ installer.
(Please note that VirusTotal results can change over time; maybe the results you saw were “preliminary”, and didn’t reflect final and full analysis.)
I clicked the “re-analyze” button, and it still shows

I don’t know what that “1 sandbox” is, but it doesn’t mention anything else about that anywhere. -
@peterjones I don’t know why we see different reports, but below I include a screenshot of the page I get (I highlighted the the items I mentioned on my original post):
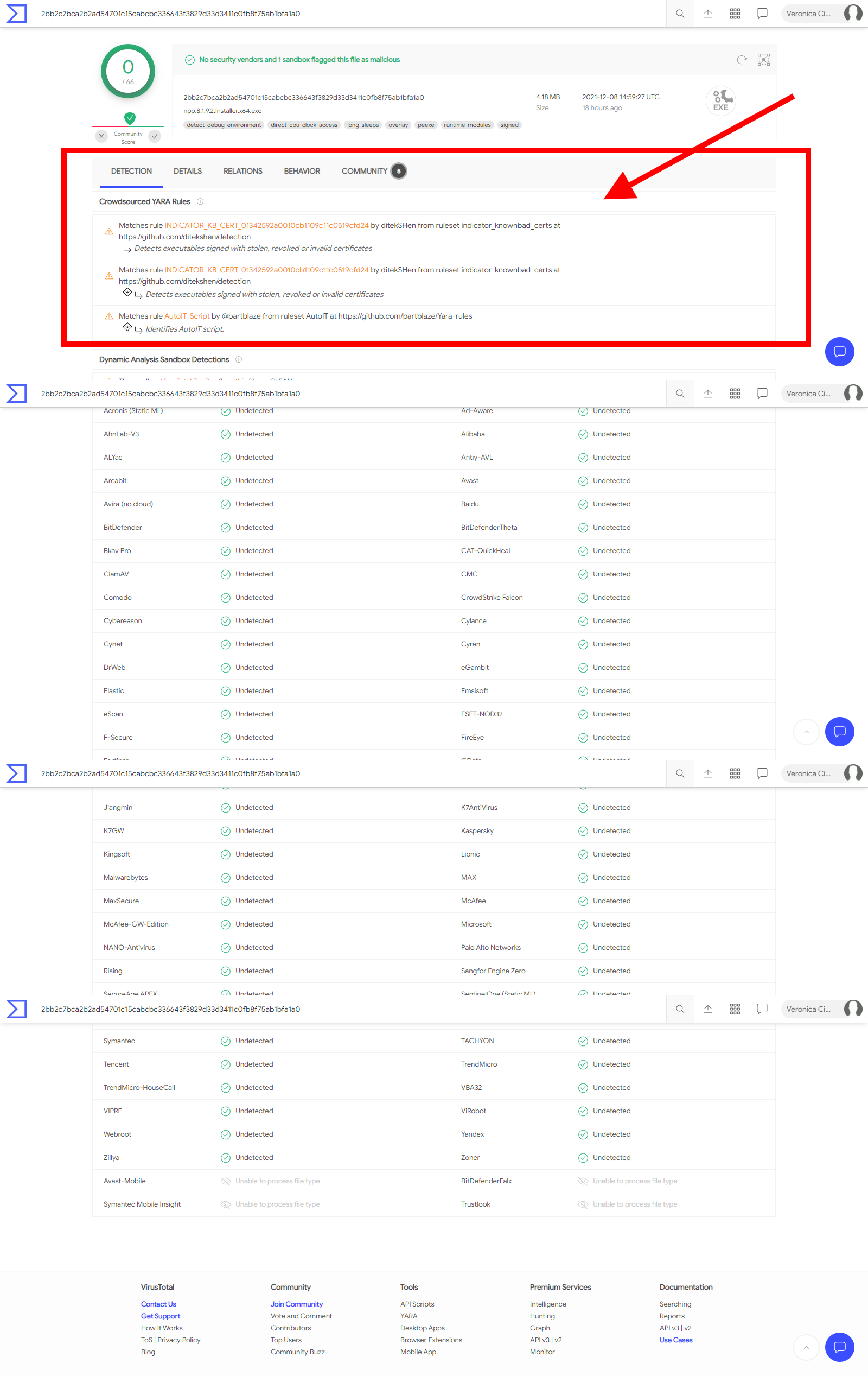
The fact that you see a different page made me curious about how the WayBackMachine (archiving the internet) would see this page, so I archived it here: https://web.archive.org/web/20211209090408/https://www.virustotal.com/gui/file/2bb2c7bca2b2ad54701c15cabcbc336643f3829d33d3411c0fb8f75ab1bfa1a0/detection
Lastly, I’ve heard a picture says more than a thousand words, and thus I know a video can be more descriptive. Here you can view a screencast as I reload the VirusTotal page: https://www.youtube.com/watch?v=uFy_SRadWTA
Please let me know your thoughts
-
Maybe it’s because you appear to be logged into VirusTotal, whereas I’m not; maybe only people logged in can see those crowdsourced rule results.
I used Windows Explorer to look at the properties of npp.8.1.9.2.Installer.x64.exe, and went to the Digital Signatures :
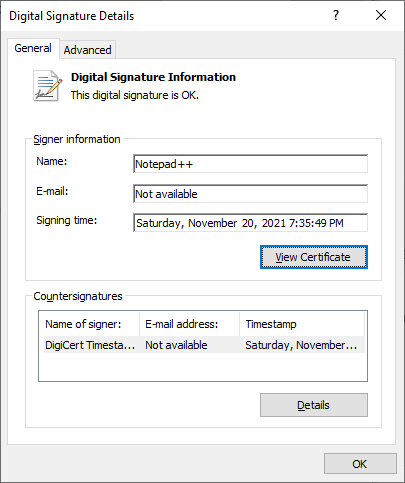
As I look through the various tabs on those certifications, I cannot see anything that would indicate that it’s expired – the Notepad++ cert is good until next year, and the cert that signed it is good until 2031.
I wonder if whoever ran that check doesn’t have an up-to-date certificate list on their end, so they maybe don’t have DigiCert’s newest signing certificate for verification.
That said, it’s also rather irrelevant, because the next version of Notepad++ is already released/
-
I believe this is something you need to take up with owner of the ‘detection’ rules. My guess is that their rule is not robust enough and has tripped over a false-positive match based on an incorrect hash or checksum calculation.
FWIW:
I scan all Notepad++ downloads with the most current signature files in ClamWin at the time of download and they were clean then. As @peterjones did with the installer, I submitted the npp.8.1.9.portable.x64.7z file to VirusTotal and received a report that it had been first scanned 3 days ago and no vendors raised any flags and the SHA256 file checksum reported matches the one published by the developer. I also re-scanned the npp.8.1.9.portable.x64.7z file using the most recent ClamWin signature updates and it was also passed as ‘not infected’.During my infrequent use of the online anti-malware scanners I have come across the occasional false positive detection in 1 or 2 of the 20 or so scanners at a particular site. As I understand it, the detection process is based on hashed signature matching of key parts of binary files and it is not fool-proof in either direction.
BTW: I draw the line at three engines at any site detecting malware and immediately delete the tested file otherwise I submit the file to a second detection site. If I’m really interested in the download, I break the archive/executable apart and check each binary component as sometimes the detection is triggered by a ‘possibly dangerous tool’, e.g., a privilege escalation wrapper for an installer or a serial number extractor bundled in the archive.
-
Maybe this has something to do with this?
If that is the case, then that is on the user for not downloading it from official/reputable places and has nothing to do with Notepad++ really, as it has no control on where the user get these files from.
-
@digital-streaming
Just as a point, since I’m not real sure, but you may be experiencing one of the issues as reported about the Log4J exploit, per Apache’s reports, here where it claims there can be:
Improper validation of certificate with host mismatch in Apache Log4j SMTP appender. This could allow an SMTPS connection to be intercepted by a man-in-the-middle attack which could leak any log messages sent through that appender.Just an FYI.
Lee
-
@imspecial SO I downloaded the file from: https://github.com/notepad-plus-plus/notepad-plus-plus/releases/download/v8.1.9.2/npp.8.1.9.2.Installer.x64.exe
Is this a rogue distributor?
The SHA256 of the file I got is: 2bb2c7bca2b2ad54701c15cabcbc336643f3829d33d3411c0fb8f75ab1bfa1a0 What is the SHA256 of a bonafide npp.8.1.9.2.Installer.x64.exe file?
Thx
-
@lycan-thrope Wow… good point. Although I don’t have Apache on my system (the man in the middle might) but I think the “Improper validation of certificate with host mismatch” is a symptom of other malware too. And yes, I am the victim of persistent hacking, and no matter what I do I can’t shake it off.
-
@digital-streaming said in VirusTotal.Com Analysis of npp.8.1.9.2.Installer.x64.exe Reports "Detects executables signed with stolen, revoked or invalid certificates":
@imspecial SO I downloaded the file from: https://github.com/notepad-plus-plus/notepad-plus-plus/releases/download/v8.1.9.2/npp.8.1.9.2.Installer.x64.exe
Is this a rogue distributor?
No, the official github repo is not a rogue distributor.
The SHA256 of the file I got is: 2bb2c7bca2b2ad54701c15cabcbc336643f3829d33d3411c0fb8f75ab1bfa1a0 What is the SHA256 of a bonafide npp.8.1.9.2.Installer.x64.exe file?
You could look on the official notepad-plus-plus.org website: the download page for 8.1.9.2 has a link to the “sha256 digests of binary packages”, which you can download (it’s a text file, though it doesn’t have the
.txtextension), which contains the following:4151d4d023e8f2cbb41bbeb7fd07b5fa0f72004356f8458c494ab39f758e9c4e npp.8.1.9.2.portable.7z 4c9dc6847fc84c03b908d57992985334409bd905596759761b1bf6e593255482 npp.8.1.9.2.portable.arm64.7z 8bc7656790317fe1cf0c21eb0d650a0e9159edf4a8adfcbf89c7b2317941d494 npp.8.1.9.2.portable.minimalist.7z 9a56cdda39dd7d46b312f25600011832e2c9642ced82b1b215c7f5f703e1be50 npp.8.1.9.2.portable.minimalist.arm64.7z 65ca67909e7fe2fb980771c253b7ae08b2bd31f29bf7ecbd43d17ee3dbfc1d9f npp.8.1.9.2.portable.minimalist.x64.7z 75cbd8721bfe795c0996cb319452e49f93fbd204062510f7ea30e7e21714cc8b npp.8.1.9.2.portable.x64.7z d1e9e2507a298c4390e334da6001629b5e4f1b562774c323fa24c3db1a5b0465 npp.8.1.9.2.Installer.arm64.exe a762e97b4f3387da0d273d692da16d34fbb8fbfdc8c07b04c3c837ff33220f00 npp.8.1.9.2.Installer.exe 2bb2c7bca2b2ad54701c15cabcbc336643f3829d33d3411c0fb8f75ab1bfa1a0 npp.8.1.9.2.Installer.x64.exe 44ecafab5f6f9f1e9dde7ed69eb7c19d45ae657bce4350888a7cf5b1d70a5d84 npp.8.1.9.2.portable.arm64.zip 56167f3d71cb71b4b1f6859c557614d84eda158a0a1ccd5ac9217abb9c530975 npp.8.1.9.2.portable.x64.zip d84c071dfbcc136166ae9e0b4545c3d975e07db2b9b6a5f2b481475dbb8e4532 npp.8.1.9.2.portable.zipIn that list, you will find that the SHA256 you quoted matches the SHA256 in the list for that binary.
Or, since you got it from the official github repo, look at the same page in that repo where you downloaded the binary: https://github.com/notepad-plus-plus/notepad-plus-plus/releases/tag/v8.1.9.2 … and note that it shows the same list of SHA256 signatures
But the whole point of those is that you’re not supposed to take my word for it. Go to the official website for the product, click on the links found there, and compare
-
@imspecial said in VirusTotal.Com Analysis of npp.8.1.9.2.Installer.x64.exe Reports "Detects executables signed with stolen, revoked or invalid certificates":
Maybe this has something to do with this?
If that is the case, then that is on the user for not downloading it from official/reputable places and has nothing to do with Notepad++ really, as it has no control on where the user get these files from.
Actually I was just addressing what I quoted above. I thought it would be a good idea to get your feedback on the file’s hash and the location of the download which I included in the original post.
Thx